44 aws best practices
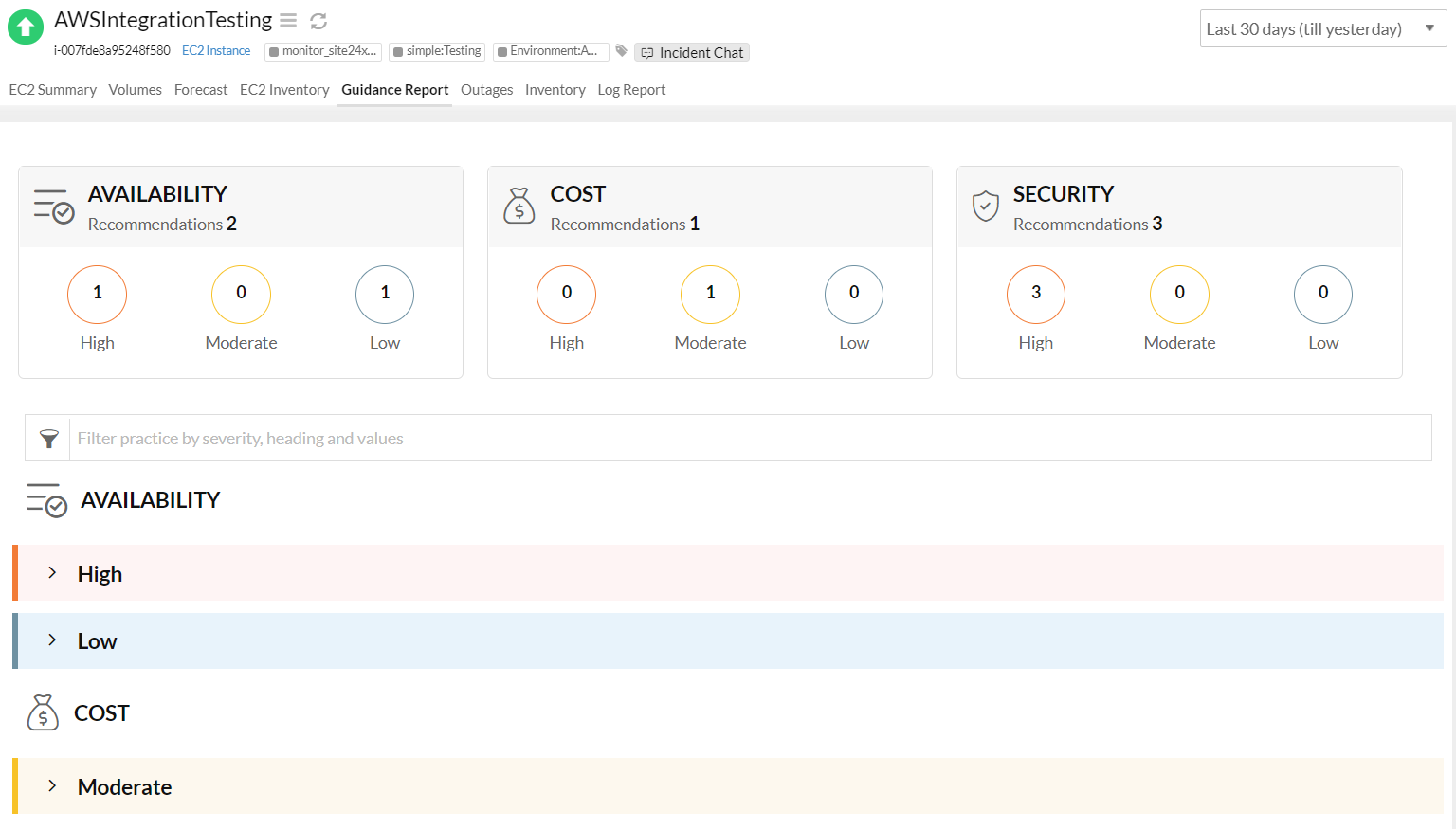
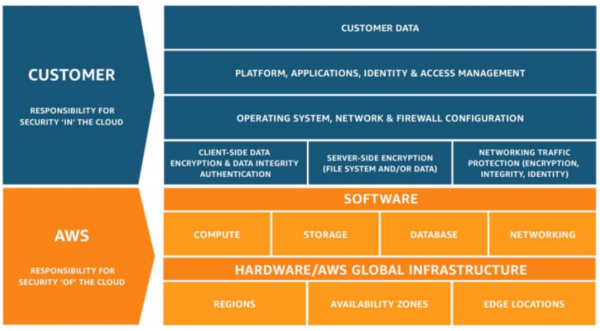
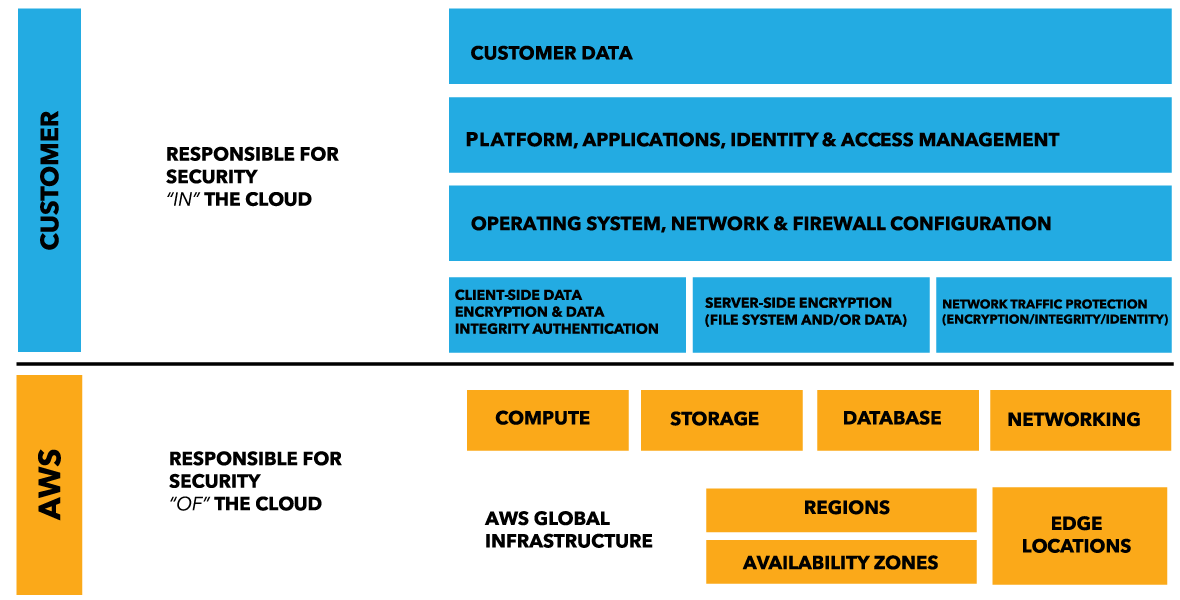
AWS VPC Security: 13 Best Practices [The 2022 Guide] - Hyperglance The best practice is to split your production, staging, and pre-production environments across different VPCs. Image courtesy of AWS 5. Use Security Groups To Control Resource Access It's vital that you factor in AWS Identity Access Management (IAM) when you're planning and setting up your VPC. PDF AWS Security Best Practices Amazon Web Services AWS Security Best Practices Page 2 Know the AWS Shared Responsibility Model Amazon Web Services provides a secure global infrastructure and services in the cloud. You can build your systems using AWS as the foundation, and architect an ISMS that takes advantage of AWS features.
10 Best Practices for AWS Cost Optimization - Whizlabs Blog Among the prominent best practices for AWS cost optimization, it is essential to reflect on the optimization of network costs. The Trusted Advisor Idle Load Balancers check tool can help you find a report of load balancers with RequestCount lower than 100 in the last 7 days.

Aws best practices
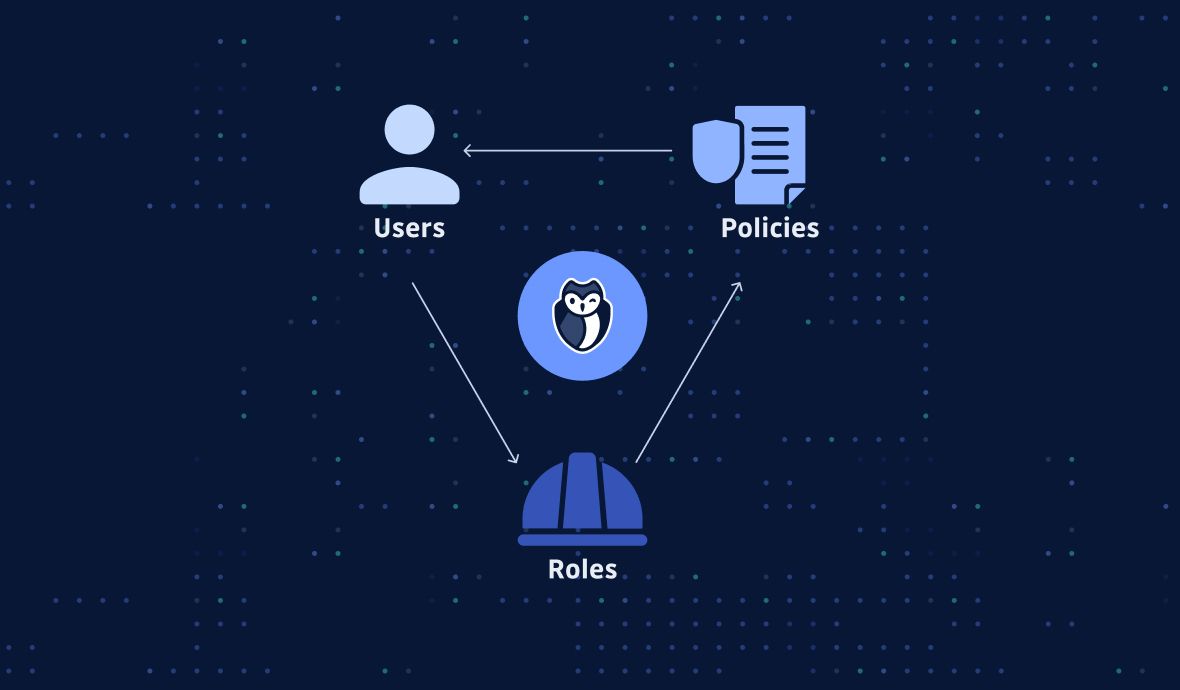
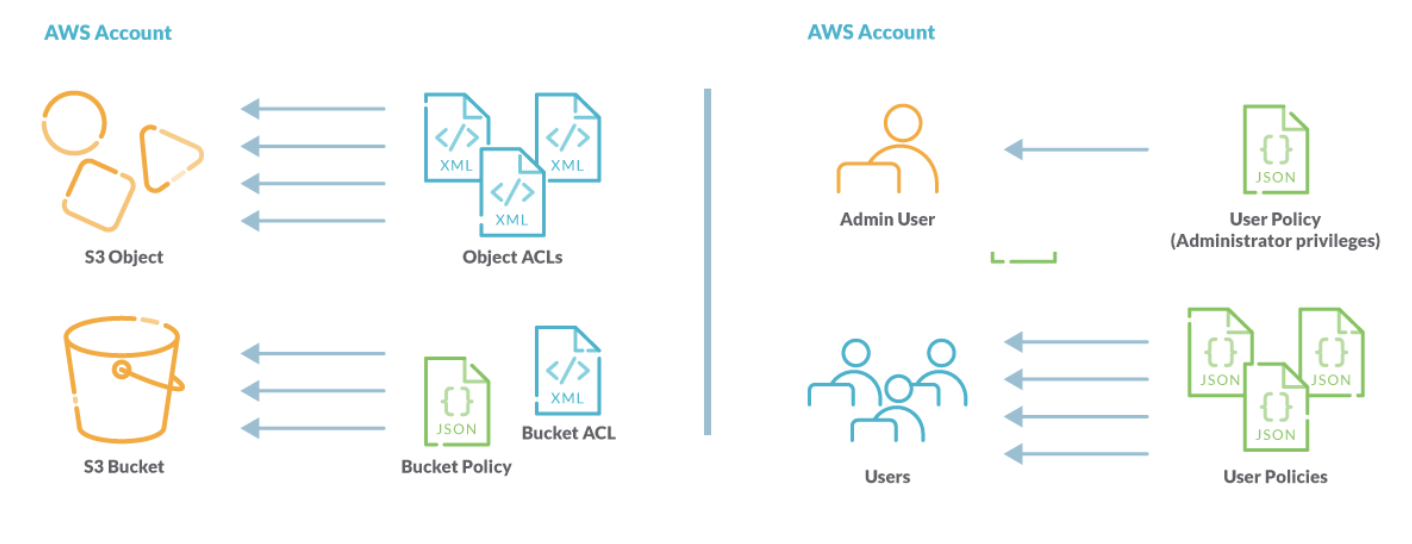
Best practices for Amazon EC2 - Amazon Elastic Compute Cloud How the AWS binary blob is created Find a Linux AMI Shared AMIs Find shared AMIs Make an AMI public Share an AMI with organizations or OUs Share an AMI with specific AWS accounts Use bookmarks Guidelines for shared Linux AMIs Paid AMIs AMI lifecycle Create an AMI Create an Amazon EBS-backed Linux AMI Create an instance store-backed Linux AMI 13 AWS IAM Best Practices for Security and Compliance To help you make the most of Amazon's built-in controls, we've compiled the top 13 AWS IAM best practices every organization should follow. 1) Restrict use of the AWS root account When you register an account with AWS, the initial user account created is known as the root account. Best practice rules for AWS Identity and Access Management (IAM) Best practice rules for AWS Identity and Access Management (IAM) AWS Identity and Access Management (IAM) enables you to manage users and permission levels for staff and third parties requiring access to your AWS account. This service provides centralized access to manage access keys, security credentials, and permission levels.
Aws best practices. What is Data Management? - Data Management Explained - AWS Data management best practices form the basis of a successful data strategy. The following are common best practices. Team collaboration. Business users and technical teams must collaborate to ensure that an organization's data requirements are met. All data processing and analysis should prioritize business intelligence requirements. AWS Root Account Best Practices | Logicata AWS (Amazon Web Services) root user best practices are similar to those for any AWS user with high-level permissions. However, as the root user is a particularly high-level user, it requires extra care and oversight to keep safe. At Logicata, we frequently help our customers secure their AWS accounts as part of our InfrAssure managed AWS service. Introduction to AWS — Cloud Best Practices - Cup of Code Security Best Practices. Here we will touch on security in a nutshell, and I recommend reading my AWS security dedicated blog post for more coverage. Let's go over AWS's security best practices: Use AWS features for defense-in-depth: Defense in depth is a strategy that leverages multiple security measures to protect an organization's ... Reliability - AWS Well-Architected Framework There are four best practice areas for reliability in the cloud: Foundations Workload Architecture Change Management Failure Management To achieve reliability you must start with the foundations — an environment where service quotas and network topology accommodate the workload.
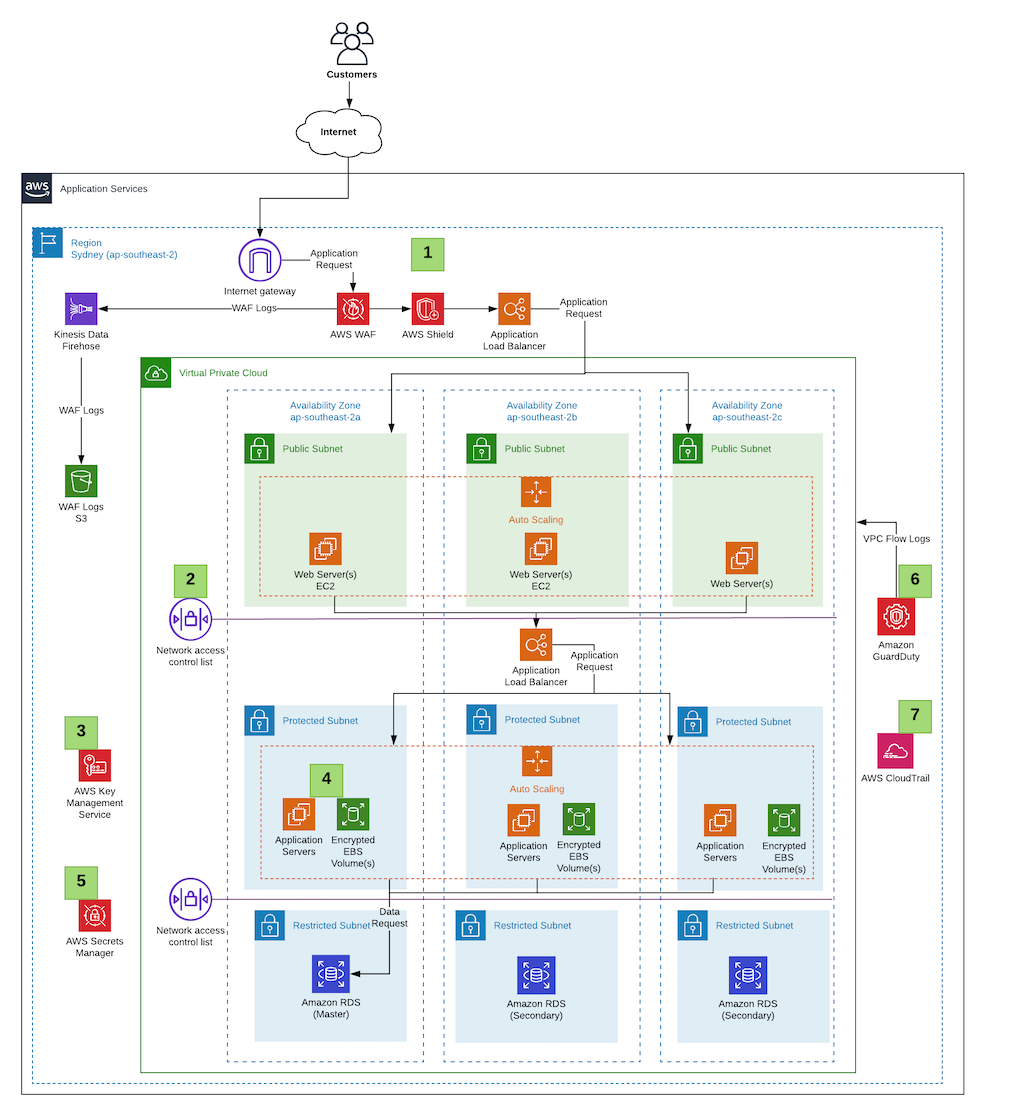
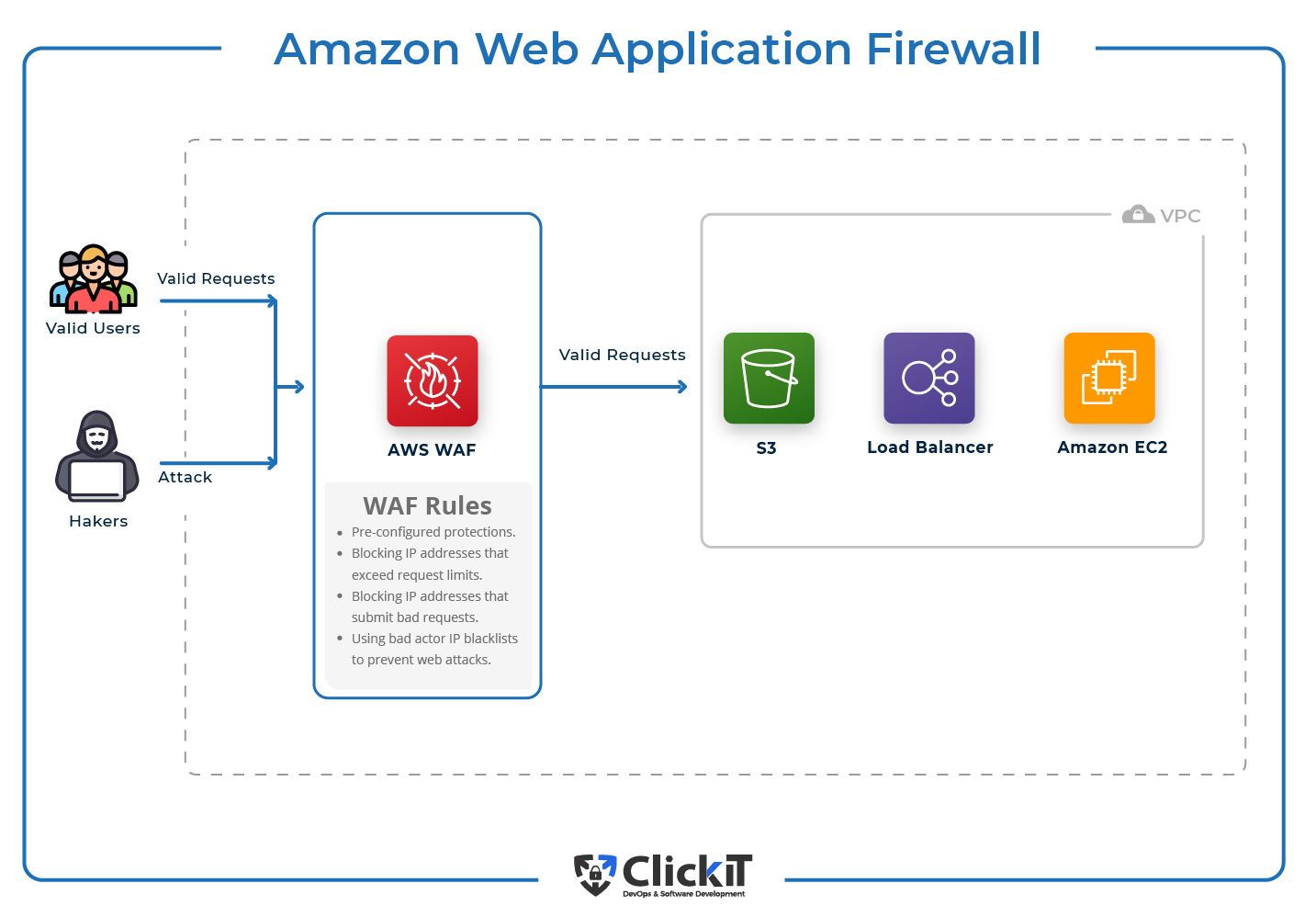
AWS Best Practices: five key approaches - Cloud Academy AWS Best Practices: secure your Applications Sometimes it is better to explain a concept with a picture or diagram rather than with words. The diagram below could be a small scale deployment on AWS. You have a Web Server, an App Server, and a DB server. You should allow access from the outside world only where necessary. 51 AWS Security Best Practices | McAfee Blog Below are some best practices around AWS database and data storage security: Ensure that no S3 Buckets are publicly readable/writeable unless required by the business. Turn on Redshift audit logging in order to support auditing and post-incident forensic investigations for a given database. Encrypt data stored in EBS as an added layer of security. An introduction to AWS IAM best practices - SearchCloudComputing Here are some best practices to enhance IAM effectiveness and help avoid common security mistakes. Never use root credentials. A business might create a single AWS account with root credentials and then establish many different users and roles with other credentials. PDF Amazon EMR Best Practices - d0.awsstatic.com The following scenarios explain three ways to optimize data migration from your current local storage location (data center) to AWS by fully utilizing your available throughput. Scenario 1: Moving Large Amounts of Data from HDFS (Data enter) to Amazon S3
Getting Started: Follow Security Best Practices as You Configure Your ... Following security best practices can help prevent your root account from being compromised, which is an important safeguard because your root account has access to all services and resources in your account. Create a strong password for your AWS resources AWS Monitoring Tools and Best Practices: Monitor What Matters - NetApp Amazon Web Services (AWS) monitoring is a set of practices you can use to verify the security and performance of your AWS resources and data. These practices rely on various tools and services to collect, analyze, and present data insights. You can then use these insights to identify vulnerabilities and issues, predict performance, and optimize ... AWS S3 to OCI access best practices - blogs.oracle.com Create AWS S3 customer keys in OCI. 1. Login to OCI tenancy and go to user profile section. 2. Go to Customer secret keys section and create public/private key pair. Note - You need to save secret key at the time of creation. 2. Change S3 designation compartment for creating new buckets. In my case I am using my own compartment. 10+ AWS Cost Management Best Practices To Implement In 2022 - CloudZero These are the AWS cost management best practices you should focus on to minimize waste: Plan and manage reserved instances (RIs)/choose the right savings plan. For reserved instances, identify underutilized EC2 instances and downgrade their size or move to a different instance family to reduce cost.
9 AWS Security Best Practices - Alert Logic 9 AWS Security Best Practices 1. Become Acquainted with the AWS Well-Architected Framework While AWS isn't responsible for the security in your cloud environment, they do offer ample resources to help you protect your AWS workloads. If you're new to building on AWS, one of the first things you should read is the Well-Architected Framework.
Best Practices for Securing your Amazon EC2 Instances Why should one follow best practices while using AWS EC2? There can be multiple dimensions while talking security of the cloud. It is important to strike a good balance between performance, safety, and usage. No doubt, AWS provides excellent security on the cloud, it secures everything from the perspective of multi-tenancy and virtualization.
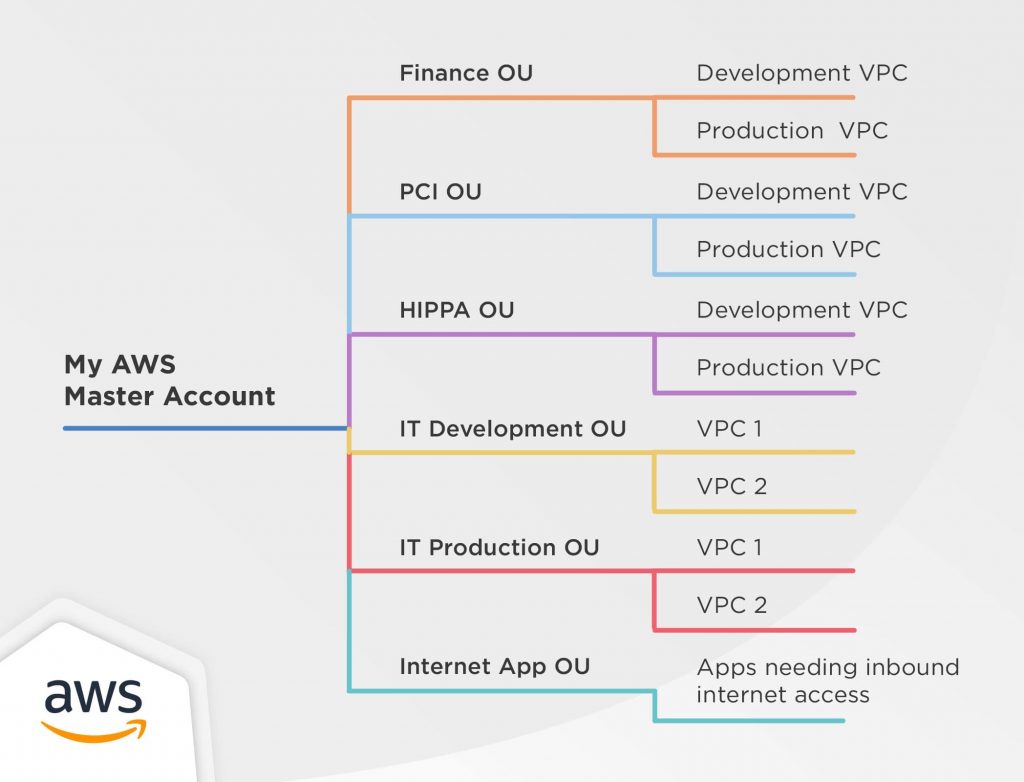
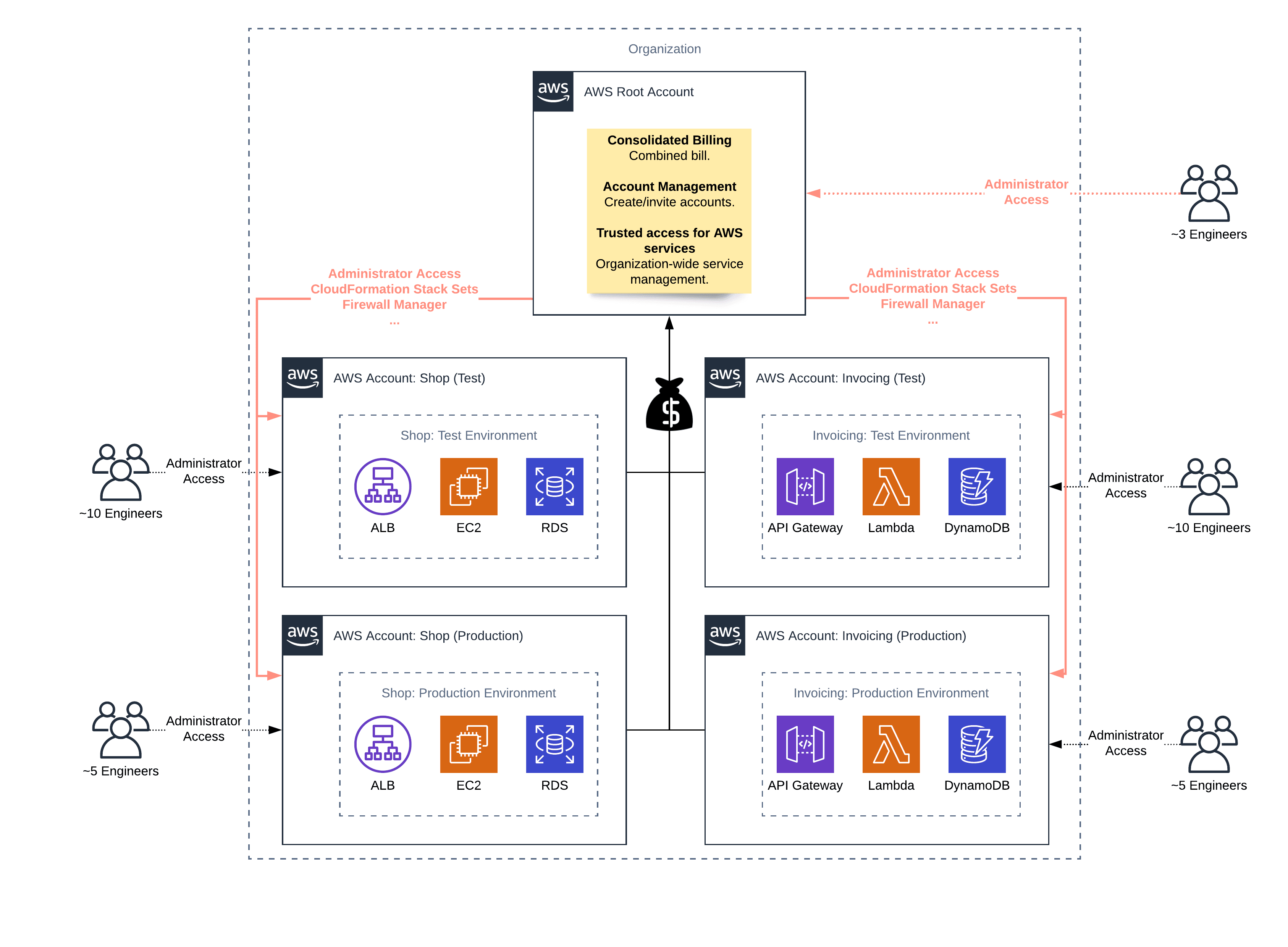
Establishing your best practice AWS environment Using a multi-account environment is an AWS best practice that offers several benefits: Rapid innovation with various requirements - You can allocate AWS accounts to different teams, projects, or products within your company ensuring that each of them can rapidly innovate while allowing for their own security requirements.
AWS Tags Best Practices and AWS Tagging Strategies AWS Tags Best Practices. While there isn't a perfect AWS tagging strategy that works for every organization, there are a few AWS tagging best practices that you should be familiar with. 1. Know how each AWS tag you create will be used. AWS cites four categories for cost allocation tags: technical, business, security, and automation. Consider ...
Best practices for AWS Organizations - AWS Organizations Best practices for AWS Organizations - AWS Organizations AWS Documentation AWS Organizations User Guide Best practices for AWS Organizations PDF RSS We recommend that you follow these best practices when you create and operate your organization. Topics Best practices for the management account Best practices for member accounts
AWS Tagging Best Practices | Lucidchart Blog AWS tagging is a helpful way to organize and manage instances. But without setting your own internal rules for how tagging works, tags can be applied inconsistently and lose their value. Your organization needs to agree on AWS tagging best practices to keep everyone informed and make tagging more valuable.
AWS Best Practices for Beginners - Career Karma AWS Best Practices and Guidelines FAQ What are the six pillars of AWS? The six pillars of AWS are sustainability, cost optimization, performance efficiency, reliability, security, and operational excellence. These pillars describe the concepts, principles, and best practices used in designing by architects to onset workloads on the cloud.
aws/aws-eks-best-practices - GitHub GitHub - aws/aws-eks-best-practices: A best practices guide for day 2 operations, including operational excellence, security, reliability, performance efficiency, and cost optimization. master 2 branches 0 tags Go to file Code jicowan Merge pull request #216 from tzneal/update-best-practices 9bebee0 6 days ago 954 commits .github Update main.yml
AWS Logging Best Practices: 3 to Add to Your Checklist Best Practice #2: Pay Attention to Your Log Life Cycle Management and Log Availability. This practice is about making sure your log is available at all times and managing the life cycle of your logs properly. In other words, pay attention to where, when, and how you store, archive, and back up your log files.
PDF Architecting for the loud Amazon Web Services - Architecting for the Cloud: AWS Best Practices Page 5 Design Principles The AWS Cloud includes many design patterns and architectural options that you can apply to a wide variety of use cases. Some key design principles of the AWS Cloud include scalability, disposable resources, automation, loose coupling managed services
Best practice rules for AWS Identity and Access Management (IAM) Best practice rules for AWS Identity and Access Management (IAM) AWS Identity and Access Management (IAM) enables you to manage users and permission levels for staff and third parties requiring access to your AWS account. This service provides centralized access to manage access keys, security credentials, and permission levels.
13 AWS IAM Best Practices for Security and Compliance To help you make the most of Amazon's built-in controls, we've compiled the top 13 AWS IAM best practices every organization should follow. 1) Restrict use of the AWS root account When you register an account with AWS, the initial user account created is known as the root account.
Best practices for Amazon EC2 - Amazon Elastic Compute Cloud How the AWS binary blob is created Find a Linux AMI Shared AMIs Find shared AMIs Make an AMI public Share an AMI with organizations or OUs Share an AMI with specific AWS accounts Use bookmarks Guidelines for shared Linux AMIs Paid AMIs AMI lifecycle Create an AMI Create an Amazon EBS-backed Linux AMI Create an instance store-backed Linux AMI



























.jpg?ixlib=gatsbyFP&auto=compress%2Cformat&fit=max&q=50)


0 Response to "44 aws best practices"
Post a Comment